42% of the websites in the world use WordPress, there are some easy-to-use tools that can be useful when analyzing websites that use the WordPress platform to be designed and basically function. It is important to know the OSINT methods and tools for analyzing WordPress since it is the most used CMS for the development of websites on the Internet and this made many people make OSINT scripts.
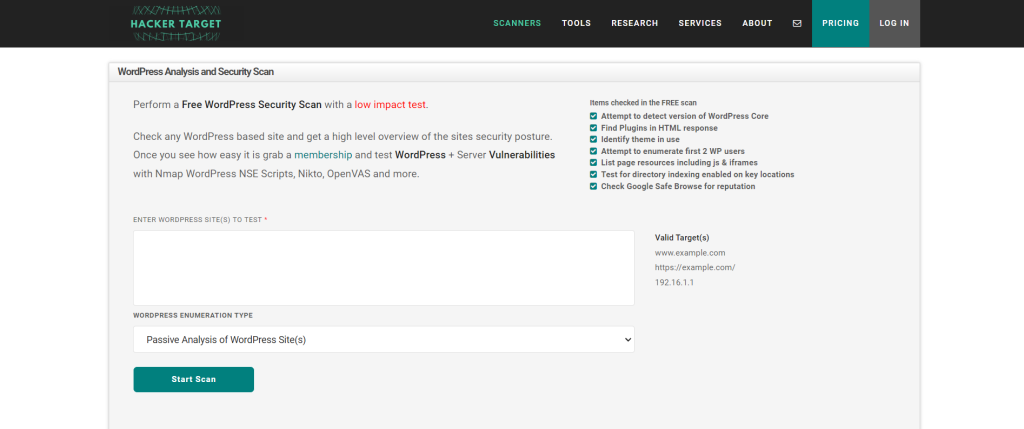
There are tools on the internet to achieve this goal, such as the website called hackertarget that has a scan for WordPress websites. There are other WordPress Scanner tools to extract information from WordPress websites. the websites called wpsec, pentest-tools and finally hackertarget. In this case we will use the tool developed by hackertarget that is available online and is easy to use.
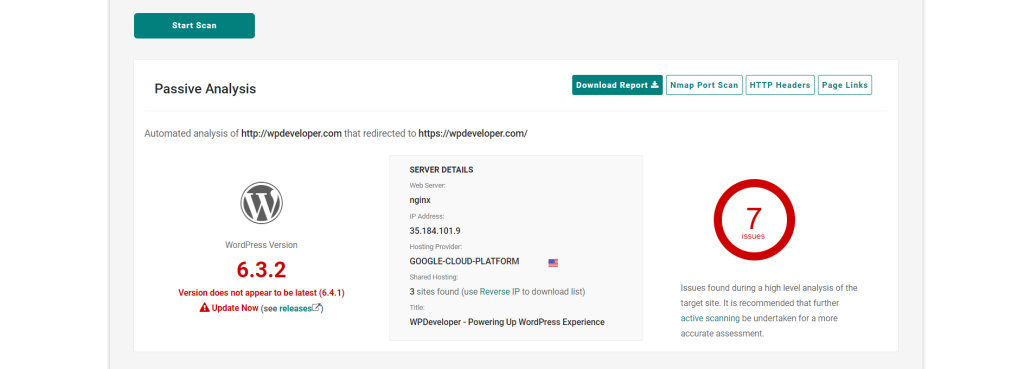
By running the scan of any website that uses WordPress, you will be able to access a lot of information on the website. including users, plugins, theme and other information
information that you can collect with OSINT methods:
- WordPress version
- IP Address
- Hosting provider
- web server
- Plugin Lists
- users lists (User Enumeration)
- WordPress Theme
- Directory Indexing
- Resources
A scan of a WordPress website can give you a lot of information, but there is certain information that is more important and that needs to be paid attention to. In this case there are 2 things where an OSINT researcher has to pay attention when analyzing a website with WordPress.
User enumeration is the tactic of viewing the registration of users who have an account on WordPress sites. This will provide usernames that can be tracked with OSINT methods. You will also get the name of users who have administrator permissions, and with the WordPress login you will be able to have the name of the user with which the administrator logs in to the admin panel.
see vulnerabilities in wordpress websites:
Seeing the vulnerabilities of a WordPress website is very important, since you could use OSINT techniques to access information from vulnerable plugins or information from the admin panel. Depending on the vulnerability and how severe it is, information such as the website administrator’s email or other information such as a remote connection to the server could be accessed.

Personally, I don’t recommend doing this. In many countries if someone does this they could have legal problems since you would be accessing information that would be considered confidential. Unless you have a court order I don’t recommend doing this.
I would only use this information if you find an extremely illegal website. Since if you get useful information for the authorities, they will thank you.





