
wpscan is a tool written and programmed in the Ruby programming language that can give OSINT researchers information about websites that use the WordPress platform as a base. This tool is for advanced OSINT users. Since to use it you will need to know about terminal commands and how to run a script in a Linux-based terminal. which is not difficult.
This tool will only work for consoles or terminals, so you need to install it. If you are a user of a Linux operating system such as Ubuntu, Linux Mint, Kali Linux or Manjaro Linux, this will be easy.
Ubuntu / Linux Mint / Kali Linux:
sudo apt install rubysudo apt install build-essential libcurl4-openssl-dev libxml2 libxml2-dev libxslt1-dev ruby-dev libgmp-dev zlib1g-devsudo gem install wpscanArch Linux: (Linux Manjaro / elementary os):
sudo pacman -S wpscanThese tutorials are for users who are on operating systems based on Debian or Arch Linux. If you have another operating system based on Linux, I recommend looking for a tutorial on the google based on your operating system. The first thing you have to do after installing wpscan is add the following command in the terminal:
wpscan --updatewpscan --url example.comAfter checking if there is an update, you have complete freedom to scan any website on the Internet that has a WordPress platform.
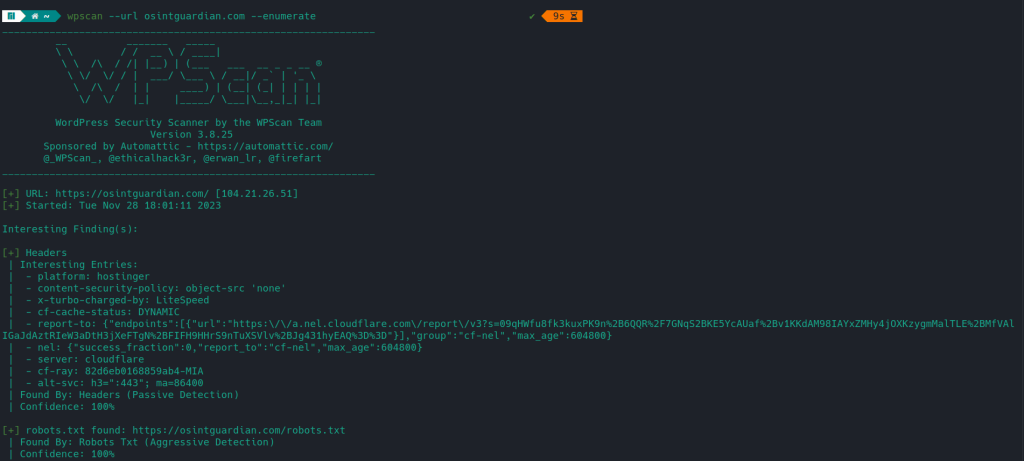
Once installed and used for the first time, these are the functions that this tool has. such as detecting user accounts on WordPress-based websites or checking the theme name and list of installed plugins on the website.
- Users enumeration
- List installed plugins and view versions
- installed theme name
- Enumerating Vulnerable Plugins
- WordPress version
With the user enumeration you will be able to see the usernames of the accounts registered on a WordPress website. This includes the administrator account and other accounts that have access to the settings of the WordPress-based website.
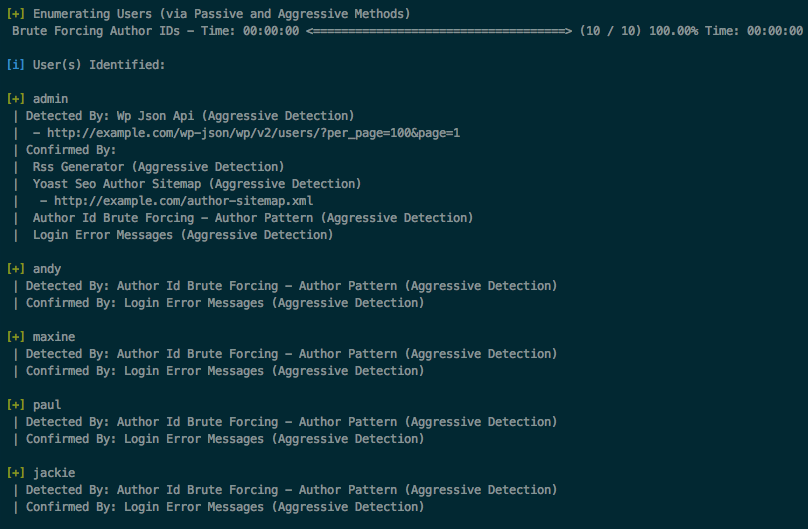
With this you can analyze and see usernames. and with OSINT methods see if that username is linked to an account from an email provider.
wpscan --url example.com --enumerate uAlso with this wpscan function you can locate and analyze usernames that the website admin did not want to be seen to the public. as a second administrator or a user with special access to the website. wpscan can detect vulnerable plugins and vulnerabilities in relation to the version of WordPress

wpscan --url example.com --enumerate vp --api-token APITOKENCODETo obtain the WPScan API you have to go to the tool’s website and create an account or log in if you already have one. Then you will be automatically redirected to your profile and you will have access to the WordPress Token API code.
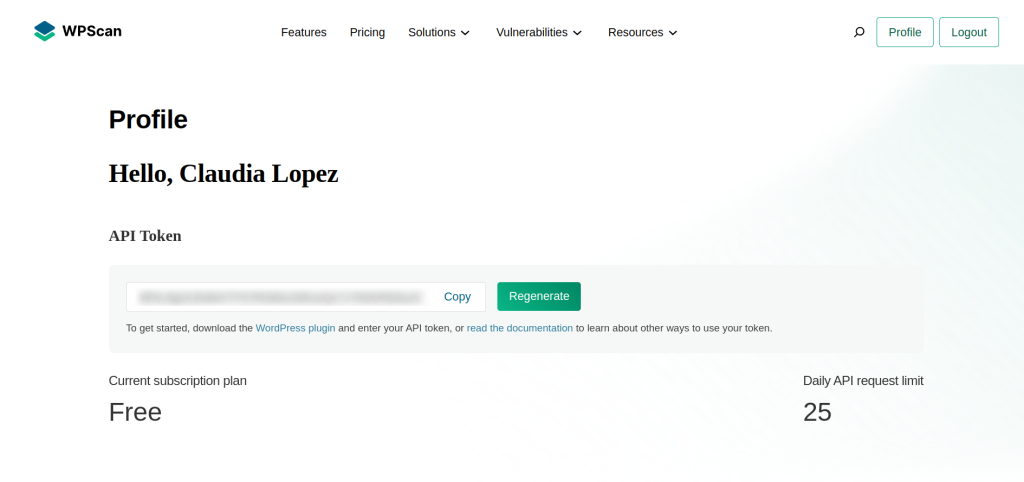
In the terminal when using the wpscan tool you have to add the line “–api-token” and your token code next to it. With the token you can have an API of the WPScan vulnerability database and detect even more vulnerability in WordPress websites. and with all these commands and all these functions, you will be able to obtain a lot of information in an investigation with OSINT methods.
wpscan --url example.com --api-token APITOKENCODE




